Fixing WiFi Multicast Flooding in bridged networks
Thu 21 September 2017I'm using MPD and PulseAudio's RTP multicasting to get a seamless multi-room audio experience.
Unfortunately, if you're using a network bridge to connect your wired and wireless LAN, using multicast RTP might have unintended consequences: All WiFi clients are flooded with multicast traffic, which can bring down the entire wireless network.
When multicast transmission arrives at the receiver's LAN, it is flooded to every Ethernet switch port unless flooding reduction such as IGMP snooping is employed (Section 2.7). (RFC 5110, Section 2 "Multicast Routing", page 4)
If you don't wanto to set up IGMP snooping, you have two alternatives: You can either
- un-bridge Ethernet and WiFi interfaces and switch to a routed approach, or
- filter out multicast packets on their way from wired interface to wireless.
Since (1) has other implications that I'd rather avoid (e.g. blocking broadcast traffic, too, so that service autodiscovery won't work anymore), so I chose the second approach.
This can easily be achieved using ebtables, which allow link layer filtering on Linux bridge interfaces.
My router is running OpenWRT, which does not with ebtables by default, so it needs to be installed first:
# opkg update
# opkg install ebtables
This is how my bridge setup looks like:
# brctl show
bridge name bridge id STP enabled interfaces
br-lan 7fff.12345678abcd no eth0.1
wlan0
wlan1
br-wan 7fff.12345678abcd no eth0.2
eth0.1, wlan0 and wlan1 are bridged. It's a dual band router that has wifi
interfaces for both the 2.4 GHz (wlan0) and the 5 GHz band (wlan1).
Now the filter rules need to be added. One rule for each wifi interface is necessary:
# ebtables -A FORWARD -o wlan0 -d Multicast -j DROP
# ebtables -A FORWARD -o wlan1 -d Multicast -j DROP
These rules tell ebtables to drop all Multicast packets if their output
device in either wlan0 or wlan1.
The effect is immediately noticeable. Before setting up multicast filtering the wifi interfaces were quite busy:
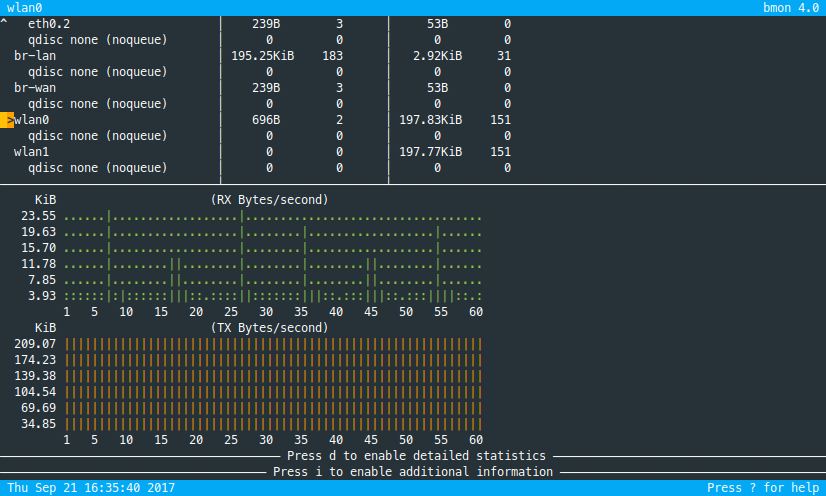
Afterwards, there's a lot less going on:
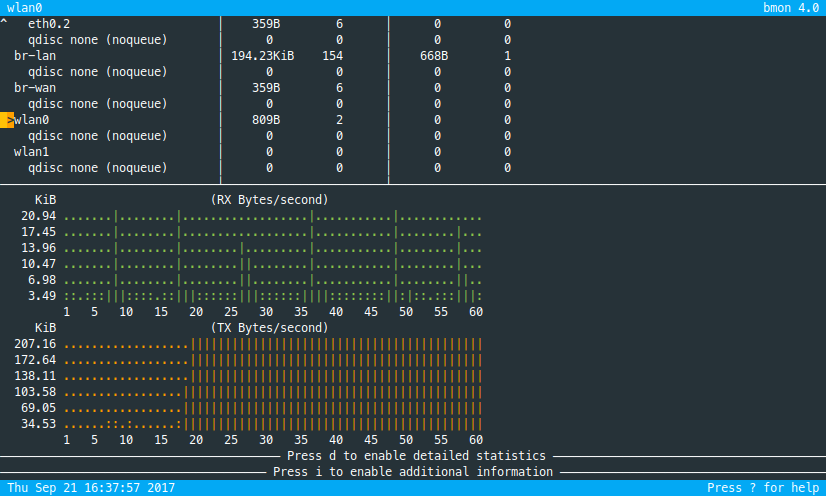
To make the filtering permanent, simply add the ebtables commands to
/etc/firewall.user.